For all embedded Linux developers, cross-compilation toolchains are part of the basic tool set, as they allow to build code for a specific CPU architecture and debug it. Until a few years ago, CodeSourcery was providing a lot of high quality pre-compiled toolchains for a wide range of architectures, but has progressively stopped doing so. Linaro provides some freely available toolchains, but only targetting ARM and AArch64. kernel.org has a set of pre-built toolchains for a wider range of architectures, but they are bare metal toolchains (cannot build Linux userspace programs) and updated infrequently.
To fill in this gap, Bootlin is happy to announce its new service to the embedded Linux community: toolchains.bootlin.com.
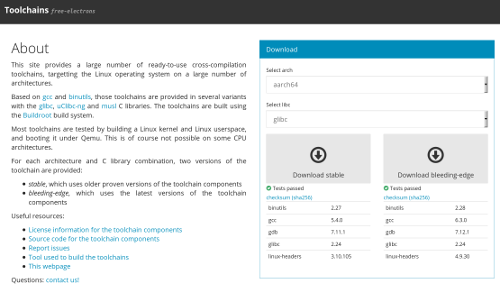
This web site provides a large number of cross-compilation toolchains, available for a wide range of architectures, in multiple variants. The toolchains are based on the classical combination of gcc, binutils and gdb, plus a C library. We currently provide a total of 138 toolchains, covering many combinations of:
- Architectures: AArch64 (little and big endian), ARC, ARM (little and big endian, ARMv5, ARMv6, ARMv7), Blackfin, m68k (Coldfire and 68k), Microblaze (little and big endian), MIPS32 and MIPS64 (little and big endian, with various instruction set variants), NIOS2, OpenRISC, PowerPC and PowerPC64, SuperH, Sparc and Sparc64, x86 and x86-64, Xtensa
- C libraries: GNU C library, uClibc-ng and musl
- Versions: for each combination, we provide a stable version which uses slightly older but more proven versions of gcc, binutils and gdb, and we provide a bleeding edge version with the latest version of gcc, binutils and gdb.
After being generated, most of the toolchains are tested by building a Linux kernel and a Linux userspace, and booting it under Qemu, which allows to verify that the toolchain is minimally working. We plan on adding more tests to validate the toolchains, and welcome your feedback on this topic. Of course, not all toolchains are tested this way, because some CPU architectures are not emulated by Qemu.
The toolchains are built with Buildroot, but can be used for any purpose: build a Linux kernel or bootloader, as a pre-built toolchain for your favorite embedded Linux build system, etc. The toolchains are available in tarballs, together with licensing information and instructions on how to rebuild the toolchain if needed.
We are very much interested in your feedback about those toolchains, so do not hesitate to report bugs or make suggestions in our issue tracker!
This work was done as part of the internship of Florent Jacquet at Bootlin.

Great work, thanks a lot!
I guess the host architecture is x86?
Do you plan to enable exotic toolchains like building ARM on POWER?
For now, our toolchains are built for x86-64 as a host machine. We already have an issue filled in asking whether we will provide toolchains running on x86 (32 bits) systems, see https://github.com/bootlin/toolchains-builder/issues/3. x86 32 bits would definitely be possible, though I’m wondering who is using x86 32 bits systems these days when you need to build things.
Regarding situations like ARM on Power, since Buildroot doesn’t support Canadian build, we would need access to a Power system to natively build the toolchains. If such access was provided, we could think about adding this, but I’m not sure how many people are realistically going to need a Blackfin toolchain that runs on POWER for example.
Thanks.
This is a generous thing that you do, and is really needed since CodeSourcery has stopped providing freely available toolchains.
Hi
I really appreciate your efforts.
In order to supplement this post please provide some information on how you tested the tools. Building tools is one think but delivering tested tools is a much wider scope.
I always preferred to use pre-built tools for Buildroot and Yocto. I wish this was possible.
And I wish a company like yours will be able to become the binary tools defacto standard like CodeSourcery at the past.
Ron.
Thanks for your comments. Regarding the testing, there is a full paragraph covering exactly this topic in our blog post. Did you miss it? Here is what we say:
After being generated, most of the toolchains are tested by building a Linux kernel and a Linux userspace, and booting it under Qemu, which allows to verify that the toolchain is minimally working. We plan on adding more tests to validate the toolchains, and welcome your feedback on this topic. Of course, not all toolchains are tested this way, because some CPU architectures are not emulated by Qemu.
So there is some amount of testing today, in that we make sure that the toolchains are capable of building a working Linux kernel and minimal Linux userspace. But this is definitely not a complete and thorough testing of the toolchain for sure, and it’s also limited to the CPU architectures for which Qemu provides emulation.
If you have some ideas and suggestions on what sort of additional testing would be useful, we are very interested. Thanks!
Thx. Yes I missed it.
It is a good starting point.
And no I have no suggestion for testing suites.
Take care.
This is a very good resource. Thanks for your effort in filling the CodeSourcery gap!
I hope the toolchains will stay downloadable for many many years, at least the “stable” ones. This would allow to use them in production.
Did you compile them with hardening features like stack smashing protection, PIE, etc.?
In the most recent versions, yes that should be the case because Buildroot now enables PIE and SSP by default. If that’s not the case, let me know and we can have a look.